7.1 Network System Security
7.1.1 Definitions
In order to provide a common lexicon from which to work with, the following definitions are provided.
RED – A designation applied to: a) all wirelines within the terminals or data routing equipment carrying classified plain language, b) all wirelines between the unencrypted side of the on-line crypto equipment used and individual subscriber terminal equipment, c) equipment originating or terminating classified plain text language, and d) areas containing these wirelines, equipment, and the interconnecting lines.
BLACK – The designation applied to all wirelines, components, equipment, and systems which handle ONLY encrypted or unclassified signals, and areas to which no unencrypted or classified signals occur.
RED/BLACK – The concept that electrical circuits components, equipment, systems, etc. which handle classified plain language data in electrical form (RED) be separated from those which handle encrypted or unclassified information (BLACK). Under this concept the terms RED and BLACK are used to clarify specific criteria related to, and to differentiate between such circuits, components equipment, and systems, etc., and the area in which they are contained.
TEMPEST – An unclassified short name referring to investigations and studies of compromising emanations. It is sometimes used synonymously for the term “compromising emanations” (e.g., TEMPEST tests, TEMPEST inspections TEMPEST control plan).
7.1.2 System Security Policy
The design (system, hardware, and software) must fulfill the operational, maintenance, and logistic security policy of the aircraft, ship, or system, on which it is used. This policy is established by the government program manager in conjunction with the operational user. The details of this policy, which impact system designers, are provided in the program security classification guide and its references.
Some major areas capable of impacting the design are:
- The maximum classification of the data processed by each of the systems using the bus.
- The maximum classification and compartmentalization of the data transferred via the bus.
- The maximum authorized classification and compartment level of the systems connected to the bus.
- The access authorization of the various crew and maintenance personnel who will be using systems connected via the bus.
7.1.3 System Security Architecture
The data bus network operates as a time shared system between various processors and users of the data. If any of these subsystems process RED information, then the data bus network design must address three complementary security areas:
1) compromising emanations (i.e., TEMPEST), 2) encryption, and 3) trusted message routing and control. Each of these areas interacts with the other, and the system designer must determine the optimum combination to satisfy the security requirements.
System security architectures, each with different advantages and disadvantages are:
- All BLACK bus – No RED data or RED data processor is directly connected to the bus.
- ALL RED bus – All systems connected to the bus are authorized access to the highest data classification and all compartments using the bus.
- RED/BLACK Gateway – Separate all RED and all BLACK buses, as defined above, are used with a gateway to allow necessary data to securely pass between them.
- RED/BLACK Composite – On a time-share basis, the bus processes RED and BLACK data between RED and BLACK subsystems securely.
7.1.4 TEMPEST Design
TEMPEST requirements must be fulfilled by the bus interface circuitry and the transmission media (bus network) for data bus systems processing RED information. The data bus network shall fulfill the TEMPEST provisions of the following documents:
- NACSIM-5100 and NACSIM-5112 for U.S. Military Systems
- BID/01/202 (4) and BID/01/200 (Series) for United Kingdom Military Systems
- AMSG-719 and AMSG-720 for NATO Military Systems
- Equivalent national requirements for other national military systems.
7.1.5 Encryption Designs
Encryption techniques may be used by the data bus network and its associated terminal’s and processor to convert RED data into BLACK data and to isolate multiple classification levels and compartments of RED data. The specific encryption technique and system design must be approved by the government agency responsible for encryption certification. While a discussion of specific acceptable encryption techniques is beyond the scope of this Designer’s Guide and is classified, any encryption design for military systems must include the following:
- TEMPEST design to preclude compromising emanations from by passing the encryption circuitry.
- Trusted design of the encryption control, input/output and data processing circuitry, and software to preclude information compromise through failure or manipulation.
- Cryptographic key management, coordination, distribution, and zeroize techniques, circuitry and software.
- Synchronization and timing protocols.
- Encryption alarm and alarm check techniques.
7.1.6 Trusted Message Routing and Control Design
The data bus network design must fulfill the requirements of DoD 5200.28-STD, “Department of Defense Trusted Computer System Evaluation Criteria,” or national equivalent, with less than one undetected control error per 10,000 hours of operation at the maximum bus message transfer rate. Corrective control action to maintain and restore system trust must be incorporated for detected system security failures.
The data bus network can be designed to meet these requirements by using the following:
- Low bit error rate circuitry and cabling techniques.
- Parity coding of control words involved in message routing.
- Bus controller monitor to detect and correct message routing errors.
Each of the System Security Architectures, as defined in the previous sections, have individual TEMPEST, encryption, isolation, and Trusted Computer System requirements for the data bus network’s transmissions media, terminal and controller designs and gateway designs. Designers are directed to their Program’s Security Classification Guide, DoD 5200.28-STD, and the TEMPEST provisions in the aforementioned documents for assistance in determination of the design requirements.
7.2 MIL-STD-1760B Interconnect Standard for Aircraft Stores
7.2.1 Definitions
MIL-STD-1760B standard defines implementation requirements for the Aircraft/Store Electrical Interconnection System (AEIS) in aircraft and stores. The electrical signal characteristics, connectors, and interface software (messages) for US/NATO aircraft and stores have been included. For definition purposes, a store is defined as any external device attached to the aircraft and is composed of devices which separate (leave the aircraft) such as missiles and bombs, and as permanent modules such as electronics pods (e.g., ECM, LANTIRN, etc.) or fuel tanks. Retrofit systems employing 1760B stores include existing aircraft such as the F-5E, F-16A/B, B-52G/H, and the B-1B. 1760B stores will also be designed into the new ATA, ATF, EFA, FSX and LHX aircraft.
The control path for these stores is a MIL-STD1553B data bus. However, there are restrictions, selected options, and exceptions to 1553B taken within 1760B to meet the aircraft/stores interoperability that requires attention by system designers.
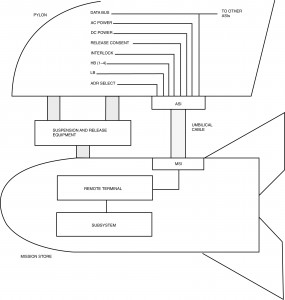
MIL-STD-1760B defines a Mission Stores Interface (MSI) as a single electrical receptacle external to the store structure. The aircraft connection is defined as the Aircraft Station Interface (ASI). Connection point examples are pylons, fuselage hard points, internal weapons bays, and wing tips. Umbilical cables connect the aircraft ASI to the store MSI. Figure I-7.1 illustrates a weapon attached to an ejector (suspension and release equipment), which is attached to a wing pylon. The primary 1760B signal set is available at the pylon ASI and connects to the store via the umbilical to the MSI. Each store uses selected signals from the available set as required. A carriage store is a device that attaches a Carriage Store Interface (CSI) to a single weapon station ASI and can interface with multiple mission stores.
In 1760B, no spare pins are available to aircraft or store designers. All interface pins in the connector are fully defined. Instead of unique signals over dedicated wires, data in 1553 word format is transmitted over a 1553 dual redundant standby bus network.
Mission stores contain embedded 1553 remote terminals. Per the standard, mission stores must be capable of BC-RT, RT-BC, and RT-RT message transfers. 1760B allows for both normal 1553 bus communication protocol (command/response) and broadcast message protocol. The aircraft has the responsibility to function as the bus controller. Due to the safety critical nature of stores, dynamic bus control is prohibited from use on a 1760B bus network.
7.2.2 Restrictions
Subaddress assignments are defined in TABLE B-l in APPENDIX B of MIL-STD-1760B. Defined subaddresses include: a) store description, b) test operations, c) nuclear store operations, d) control and monitoring, and e) mass data transfer, and f) Data wraparound. As in 1553B both mode code indicator (00000 and 11111) are required. Mission store terminals are required to implement the transmit status word, reset remote terminal, transmitter shutdown, override transmitter shutdown, transmit vector word, synchronize with data word, and transmit last command word mode codes. If the terminal flag bit is implemented, then the inhibit terminal flag mode code is required. In addition, if the service request bit is used, the data word associated with the transmit vector word mode code must be available when the bit is set. The setting of the subsystem flag bit is interpreted as a total loss of the store. MIL-STD-1760B imposes a 30 word limit on both transmit and receive messages to/from a store (see paragraph B.40.2.1 of APPENDIX B). The use of checksums in the data message is optional except for: a) Mission store control, b) Mission store monitoring messages, and c) Store description messages. All checksummed messages shall satisfy the modulo 2 arithmetic to each bit (no carries), of all data words including the checksum, the sum shall be zero.
Store initialization sequences. First communication, is defined in Paragraph 5.1.1.12.3. on page 33. The initialization procedure imposes on the network bus controller a message timing sequence to first communication no sooner then 150 milliseconds for first status response (with potential for the busy bit to be set in the status word) and up to 500 milliseconds for response of a valid store identification message. The timing reference point is 150 milliseconds after the application of power to the store (115/120V ac and 28V dc power #1). The 30 word identification message consists of: a) a one word header with a fixed hexadecimal pattern of 0421, b) a one word country code, c) nine words of store identity (e.g., AGM-131), d) Maximum interruptive BIT time with eighteen words of null characters, and e) one word of the checksum value for the message.
7.2.3 MIL-STD-1760B Signals Related to 1553B
Figure I-7.2 shows the interface signals related to the data bus system. Mux A and mux B are the 1553 transformer coupled stubs from the aircraft. The address and odd parity bits are for wiring the unique remote terminal address, which is established at the ASI connector. It is permissible for stores to latch the address upon initialization rather than continuously reading it.
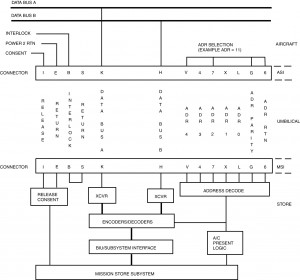
As shown in figure I-7.2, the aircraft determines the stores presence by monitoring the interlock circuitry. The store is designed to jumper the interlock signal to the interlock return signal. The circuit is broken when the store separates. The store is not permitted to use the interlock signals to determine the aircraft’s presence. The store may use the terminal address lines to determine if the aircraft is present (attached). However, since a single fault failure is possible at the address interface, the store designer should not allow safety critical functions to occur based solely upon detection of the no aircraft.
Enabling of release consent is used to signal to the store that safety critical messages arriving via the data bus are to be acted upon as valid consent from the aircraft (crew). Safety critical events include irreversible functions such as rocket motor ignition, suspension hook release, and deployment of chutes and fins. 1760B allows 10 milliseconds for the consent signal stabilization before the messages start arriving. The return reference for release consent is the return of dc power #2.
7.2.4 Data Bus Networks and Components
The network configuration depends upon the mission. The initial store load determines the number of remote terminals to be connected to the weapons network. During flight weapons are expended and removed from the bus. Since the number of remote terminals is changing, the bus loading and network reflections is also changing. Improper store separation may physically damage the umbilical. Hot rocket exhaust plume potentially could cause multiple shorts on the bus, hampering communications with the remaining stores. Since ASI and MSI connectors and umbilicals are exposed to extreme physical environments, the stubs are more likely to experience shorts than the network contained within the aircraft fuselage. Therefore, the systems designer must take special precautions when designing 1760B bus networks.
Transformer coupled stubs are required for all connections in 1760B. To be interoperable to all stores, the aircraft coupler transformer should not be canter tapped on the stub side. In order to support multiple aircraft store stations without routing the bus, coupler boxes with five to eight transformer coupled stubs are now available. This allows the bus to remain in a more protected environment, such as inside the fuselage or wing, and branch out with stubs to a cluster of external connectors at the stations.
Transceiver output voltage for the stores on the stub, is set at a minimum of 20 volts peak to peak when measured at the MSI; two volts higher than the 1553B minimum. This additional requirement on transceivers is necessary since the network paths vary from aircraft to aircraft and station to station. The ASI and MSI also cause network breakpoints that are not usually made for stubs. Constant voltage transceivers will provide a tighter control of output voltage (as opposed to constant current transceivers) as the network load changes. Current limiting of the transceiver output stage provides protection against multiple high loads on the network.
Twinax connector design is required in 1760B for both data bus signals (A and B). The coaxial data high, data low, and shield provides a protection from the electromagnetic environment (EMI, EMP, and lighting).
7.3 System 2
The System 2 specification will fully specify the electrical and logical interface for a nuclear bomb and will specify the electrical interface and part of the logical interface concerning warhead functions for missiles with nuclear warheads.
7.3.1 Significant Elements of System 2
There is one provision of paramount importance in the System 2 specification that impacts upon hardware and system designers. Remote terminal subaddresses 19 and 27 are reserved by System 2 for exclusive use by nuclear weapons. This means that NO stores bus network can have any remote terminals except nuclear weapons that use subaddress 19 or 27 for any purpose if that stores bus network is ever to be used in conjunction with nuclear weapons. This also means that non-nuclear (non-System 2) weapons must not use subaddress 19 or 27 if they are ever to be carried in a *mixed load” on the same stores bus network with nuclear weapons. This restriction is significant enough to impact most aircraft bus architectures and, unless it is absolutely unavoidable, a stores bus network should contain only stores with embedded remote terminals, remote terminals for controlling the weapon (its suspension and release equipment), and the stores fire control (equipment controlling 1760 and non-1760 signals). No other avionics should be connected to the stores bus network. The reason for this restriction is to improve nuclear safety by simplifying the control of critical functions and minimizing the possibility of interaction with other functions. For this reason, the use of an RT-RT transfer, involving either of the two restricted subaddresses, is prohibited in System 2. The use of dynamic bus control is also prohibited.
Nuclear certification becomes more difficult and costly with complex systems. Highly integrated architectures with tightly coupled subsystems necessitate nuclear certification of subsystems having no intrinsic functional involvement with the nuclear weapon, other than perhaps being connected to the same data bus network. Therefore, it is the avowed intention of the System 2 specification and the nuclear certification community to influence aircraft and systems designers to build simply connected, highly isolated, stores bus networks for nuclear stores. This purpose should not be overlooked when designing these systems.
System 2 defines its interface requirements between an aircraft system and a single nuclear weapon. The logical interface, that is the bus messages definitions, sequences, and protocols have been developed. Care should be taken before designing any stores network system (nuclear or non-nuclear) to insure that all the proper safeguards have been accounted for. Probably the first implementation will become the de facto standard for all following implementations.